It’s been a year since public companies had to start complying with new SEC cyber incident disclosure rules requiring Form 8-Ks for “material” cyber events. Law firm Paul Hastings has now released a study of 75 disclosures from 45 companies between December 2023 and October 2024. It shows a 60% increase in the number of disclosed incidents. But many of those reports actually involved incidents that were not really material, according to the SEC Cyber Incident Disclosure Report, revealing market confusion about how to determine “materiality.”

“The SEC rules set materiality as the threshold requiring disclosure, noting that information is material if ‘there is a substantial likelihood that a reasonable shareholder would consider it important in making an investment decision, or if it would have significantly altered the ‘total mix’ of information made available,'” the law firm explained. “In determining materiality, the SEC instructed public companies to evaluate both quantitative and qualitative factors, considering: immediate fallout and any longer-term effects on its operations; customer relationships; financial impact; reputational or brand perception; and the potential for litigation or regulatory action.”
“Material Incident”
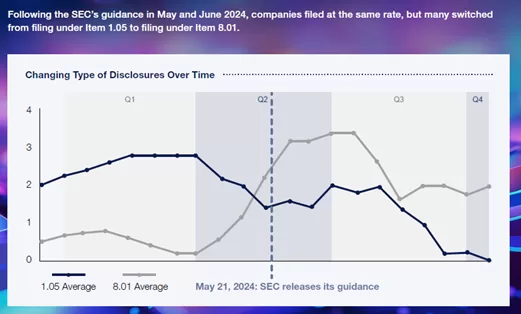
But Paul Hastings found some companies were apparently unsure what constituted a “material incident” for SEC cyber incident disclosures — a number of firms reported breaches that did not meet that threshhold. In response, the SEC in June 2024 issued guidance on how to determine whether an incident was material. The agency directed companies to start filing material cyber incidents under “Item 1.05” disclosures and non-material incidents under “Item 8.01.”
The result, as the graphic below demonstrates, was a marked increase in the share of dislosures not categorized as material (worth noting is that non-material incidents may later be revealed to be material — and the disclosure of even non-material incidents no doubt has benefits for public-market cyber security awareness.)
The report also highlights how organized, aware and brazen hacking gangs can be: “Threat actors used the SEC rules as an extortion tactic, with threat actors themselves submitting whistleblower reports to the SEC regarding failure to disclose and then publishing them online.”
“Cyber Insurance”
While not discussed in the Paul Hastings report, we’ve been covering discussion, or avoidance of discussion, of cyber insurance in SEC dislosures and related press releases. Some firms, such as Clorox, have revealed they have cyber insurance and how it will likely cover some losses from the dislosed incident. Other disclosures raise questions about how helpful the company’s cyber insurance will be. Take a 2024 disclosure from Radian Logistics Inc.: “(D)espite its current cybersecurity insurance coverage, the Company will be caused to incur substantial expenses or pay ransom in response to this incident; in which case the impact of the incident could have a material adverse effect upon the Company’s financial results and overall operations.”
For a discussion of potential risks to company executives and directors linked to cyber disclosure regulations, check out this story.
